A new feature in Firefox
With their next patch Mozilla will introduce two new features to their Firefox browser they call "DNS over HTTPs" (DoH) and Trusted Recursive Resolver (TRR). In this article we want to talk especially about the TRR. They advertise it as an additional feature which enables security. We think quite the opposite: we think it's dangerous, and here's why.
DNS? What is DNS?
The Domain Name System (DNS) is a service used in converting a computer’s host name or a Top-Level Domain (TLD) into an IP address. When you enter the domain of a website in your browser, you automatically send a request to the DNS server you have configured. The DNS server then looks up the host name and returns an IP address so your browser knows where exactly to connect to.
But here begins the problem. Not only your browser knows where exactly to connect to, but also the DNS server knows where YOU connect to. That does not necessarily have to be a problem. Basically most of the ISPs have their own DNS server that is automatically configured. And your ISP knows where you connect to anyways. So the data or information generated by their DNS server provides no additional information to them.
Why would you replace your ISP's DNS server with another one?
There are a variety of problems with the DNS protocol ("the language of DNS"). DNS requests are usually sent unencrypted and potentially everyone between you and the DNS server can read your DNS requests. Mozilla is using a new technique to transport requests over https, which encrypts the data. That is generally speaking a good thing. However usually the DNS servers that you use are local DNS servers (from your ISP) and thus the attack vector (i.e. who can spy on you) is local.
Mozilla wants to override any configured DNS server with Cloudflare
So let’s get to the new Firefox feature called "Trusted Recursive Resolver" (TRR). When Mozilla turns this on by default, the DNS changes you configured in your network won't have any effect anymore. At least for browsing with Firefox, because Mozilla has partnered up with Cloudflare, and will resolve the domain names from the application itself via a DNS server from Cloudflare based in the United States. Cloudflare will then be able to read everyone's DNS requests.
From our point of view, us being security geeks, advertising this feature with slogans like "increases security" is rather misleading because in many cases the opposite is the case. While it is true that with TRR you may not expose the websites you call to a random DNS server in an untrustworthy network you don’t know, it is not true that this increases security in general.
It is true when you are somewhere in a network you don’t know, i. e. a public WiFi network, you could automatically use the DNS server configured by the network. This could cause a security issue, because that unknown DNS server might have been compromised. In the worst case it could lead you to a phishing site pretending to be the website of your bank: as soon as you enter your personal banking information, it will be sent straight to the attackers.
Sharing data with third parties bears risks
But on the other hand Mozilla withholds that using their Trusted Recursive Resolver would cause a security issue in the first place for users who are indeed in a trustworthy network where they know their resolvers, or use the ISP’s default one. Because sharing data or information with any third party, which is Cloudflare in this case, is a security issue itself. Cloudflare publicly commits to a "pro-user privacy policy" and the deletion of all personally identifiable data after 24 hours, but you never know where your data ends up at the end of the day.

Single point of failure (SPOF)
If you are in IT, you have likely heard already about the SPOF, the single point of failure. If the SPOF breaks (like a router), the whole infrastructure will collapse. What Mozilla effectively does is adding a SPOF for all of their users. But the main problem is not that if cloudflare is down that nobody can surf anymore. No, the real problem is that it fully disables anonymity. Think about a whistleblowler who wants to send information to a newspaper. In the days before Mozilla's change, the DNS resolution was local and could be attacked. However with Mozilla's change, all DNS requests are seen by Cloudflare and in turn also by any government agency that has legal right to request data from Cloudflare.
Let's stop here for the moment and repeat: With Mozilla's change, any (US) government agency can basically trace you down.
If there is anything wrong with your government (for instance corruption, collusion or fraud) and you have information to publish about it, the government will be able to trace you down. This puts any whistleblower at risk.
What you can do is, you can configure your Firefox not to use this feature. However, it is configured to use the Cloudflare resolver as default. It’s up to you to decide, who you want to trust your data with. My local ISP seems more trustworthy to me than a big US-based corporate which acts under the guise of a selfless privacy rights defender.
Update #1: How to turn TRR off
User rendx nicely described on hackernews how to turn off TRR and we want to share this info with you:
-
Enter about:config in the address bar
-
Search for network.trr
- Set network.trr.mode = 5 to completely disable it
If you wonder about mode 5, you can find it on mozilla.org:
"Change network.trr.mode to 2 to enable DoH. This will try and use
DoH but will fallback to insecure DNS under some circumstances like
captive portals. (Use mode 5 to disable DoH under all circumstances.)"
The other modes are described on usejournal.com.
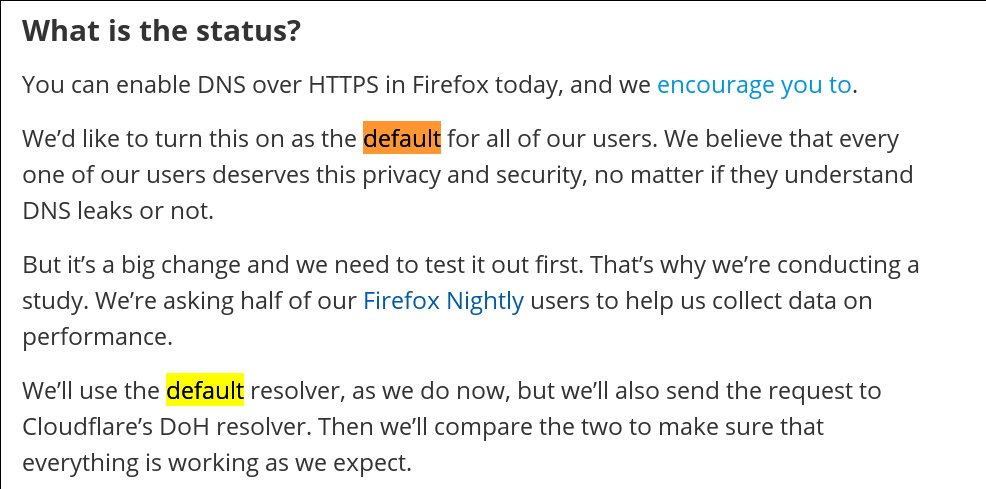
Update #2: When Mozilla makes DoH with cloudflare the default
We wrote in a previous version that "the next Mozilla patch in September" will enable DoH by default. We corrected that part as it is not clearly stated on Mozilla's blog, as can be seen in the screenshot below.